简介
我们部署完ELK Stack后,虽然可以直接浏览器访问kibana进行访问,但这样对一些重要数据来说是不安全的,可以利用密码验证设置权限访问,在Kibana所在的服务器上安装Nginx服务,利用Nginx的转发指令实现
部署Nginx
rpm -ivh Nginx-1.16.0-1.el7.ngx.x86_64.rpm
配置加密工具htpasswd生成账号和密码
htpasswd -c /etc/Nginx/ssl/htpasswd admin
New password:
Re-type new password:
Adding password for user admin
配置Nginx
cat /etc/Nginx/conf.d/kibana.conf
server {
listen 80;
#server_name kibanaes.com;
server_name paidui-kibana.360sides.net;
access_log /home/appmanager/data/logs/Nginx/kibana_access.log json;
error_log /home/appmanager/data/logs/Nginx/kibana_error.log;
location / {
auth_basic "The Kibana Monitor Center";
auth_basic_user_file /etc/Nginx/ssl/htpasswd;
proxy_pass http://1.1.1.1:5601;
proxy_http_version 1.1;
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
}
}
重启Nginx生效
Nginx -s reload
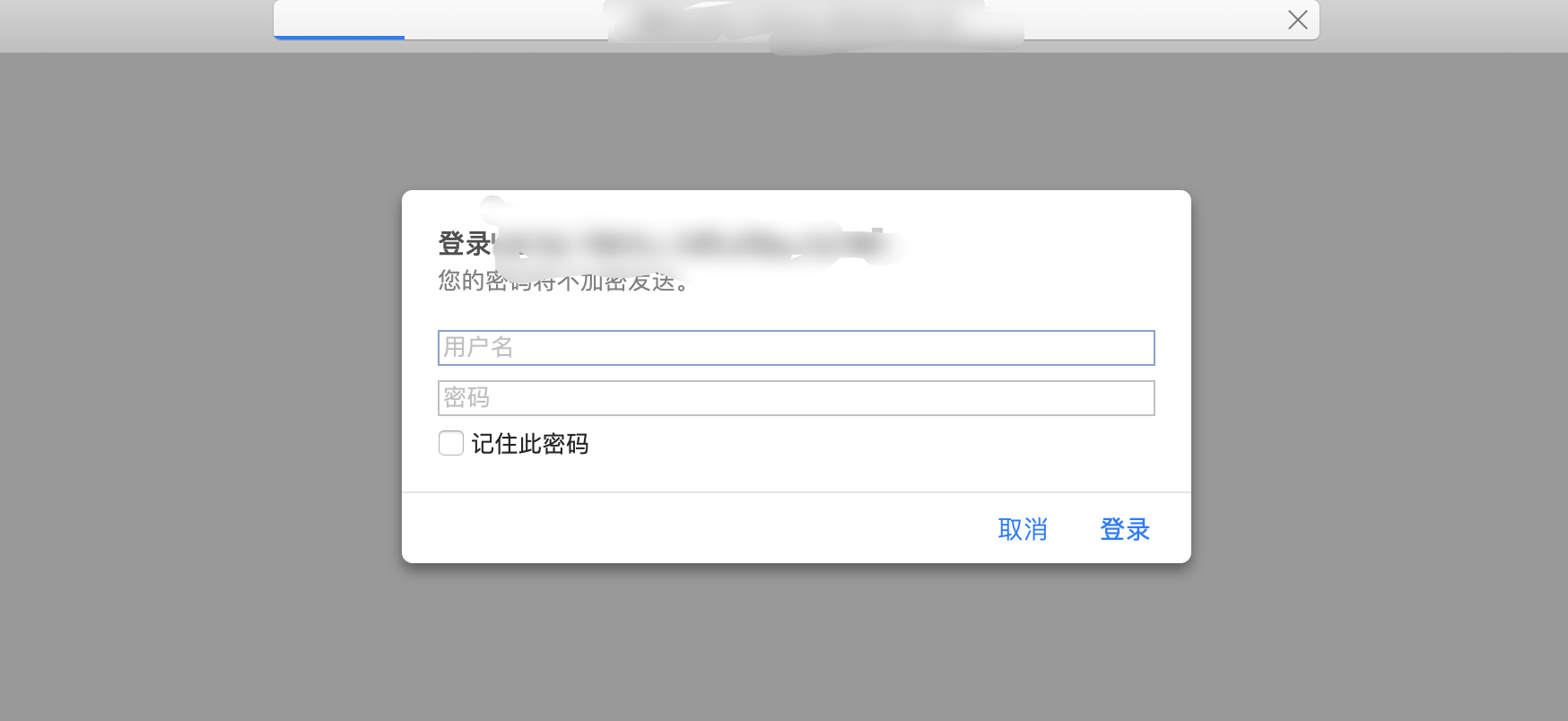
访问验证
配置本地CA生成证书加密Nginx
基于https的协议工作的一中虚拟主机,要构建这样的网站需要mod_ssl模块的支持。且需要提供两个文件:证书文件和私钥文件,证书文件是标识这个网站服务器身份的,私钥文件主要用来实现在服务器端对数据进行加密,然后在网站中传输的。证书在生产生活中需要到对应的机构去申请,在实验环境中本应该搭建一台证书服务器,然后由证书服务器给web服务器颁发证书来验证其的身份,但是证书服务器构建是非常麻烦的
生成证书及密钥文件
# 1.准备存放证书和秘钥的目录
mkdir /etc/Nginx/ssl
cd /etc/Nginx/ssl
# 2.使用openssl生成基于rsa数学算法长度为1024bit的秘钥,文件必须以key为结尾
[root@IntelID-Squid-N25 ssl]# openssl genrsa 1024 > /etc/Nginx/ssl/server.key
Generating RSA private key,1024 bit long modulus
..............++++++
..........++++++
e is 65537 (0x10001)
# 3.使用秘钥文件生成证书申请
[root@IntelID-Squid-N25 ~]# openssl req -new -key /etc/Nginx/ssl/server.key > /etc/Nginx/ssl/server.csr
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,If you enter '.',the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:BJ
Locality Name (eg,city) [Default City]:BJ
Organization Name (eg,company) [Default Company Ltd]:dx
Organizational Unit Name (eg,section) []:paidui-kibana.360sides.net
Common Name (eg,your name or your server's hostname) []:paidui-kibana.360sides.net
Email Address []:18621048481@163.com
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
# 4. 同意申请,生成证书
[root@IntelID-Squid-N25 ~]# openssl req -x509 -days 365 -key /etc/Nginx/ssl/server.key -in /etc/Nginx/ssl/server.csr > /etc/Nginx/ssl/server.crt
# -x509:证书的格式,固定的
# days:证书的有效期
# key:指定秘钥文件
# in:指定证书申请文件
配置私有CA的https
[root@IntelID-Squid-N25 conf.d]# cat /etc/Nginx/conf.d/kibana.conf
server {
listen 80;
server_name xxxx.net;
return 301 https://xxxxxx$request_uri;
}
server {
listen 443 ssl;
ssl on;
ssl_certificate /etc/Nginx/ssl/server.crt;
ssl_certificate_key /etc/Nginx/ssl/server.key;
access_log /home/appmanager/data/logs/Nginx/kibana_access.log json;
error_log /home/appmanager/data/logs/Nginx/kibana_error.log;
location / {
auth_basic "The Kibana Monitor Center";
auth_basic_user_file /etc/Nginx/ssl/htpasswd;
proxy_pass http://1.1.1.1:5601;
proxy_http_version 1.1;
proxy_set_header Host $host;
proxy_cache_bypass $http_upgrade;
}
}
Nginx -s reload